Recent cybersecurity events show that the readiness for large-scale attacks on critical infrastructures have grown dramatically. It can’t be ruled out that this is only a harbinger, or a "proof of concept" for larger attacks. A few years ago, only a few isolated attacks on hospitals, energy suppliers, etc. became known. Yet the recent ransomware wave shows how new attacks are affecting critical-infrastructure companies, and how lucrative they can be for the attacker. A web host in South Korea recently had to pay $1 million dollars in extortion, demonstrating that it is only a matter of time until similar attacks target other companies.
Digitization is advancing
Critical infrastructures, when the internal structure is looked at more closely, are often exposed to greater dangers. Because of a lack of compatibility with current operating systems, legacy systems and protocols are often used to control internal processes. Although these systems have been stable for a long time, they are exposed to immense dangers due to the lack of safety updates.
Generally, these critical infrastructures were isolated and focused on operational safety. In particular, ICS/SCADA environments are usually not regarded as security-critical units and are connected without hesitation to the office network or even to the Internet. This development is known as the digitalization of the industry, or “Industry 4.0.” Furthermore, the increasing potential of digitalization and growing internal networks is growing steadily, without the corresponding countermeasures being taken. The interdependencies and areas of influence of critical infrastructures are much higher than those of regular enterprises. Incidents in critical-infrastructure companies have a correspondingly more severe impact on everything that is directly or indirectly related to the company.
An ISMS (Information Security Management System) helps systematically to control the assets, risks, and safety measures. When implementating the ISMS using to the PDCA cycle (Plan-Do-Check-Act), critical areas and risks can be identified and protected by appropriate technical and organizational security measures. But an ISMS alone is not enough. Above all, it is important to maintain the continuity and timeliness of the defensive measures in order to keep up with the rapid development.
Not only does technology involve risks
Regardless of the general infrastructure, the German BSI (Federal Office for Information Security) calls social engineering a top risk,even before the infection by malicious software from the Internet. The reason for this is often the lack of awareness about phishing e-mails and threats throughout IT.
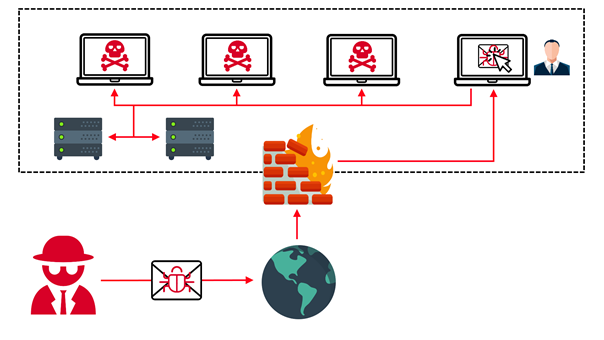
A technical analysis of the WannaCry worm reveals that in particular, unpatched systems are affected by the ransomware. However, the gaps can usually not be utilized outside the company network, since the external access points are protected by existing security infrastructure. As the worm can only propagate further within the company's infrastructure, it is generally introduced into the company by means of social engineering, in the form of phishing e-mails or USB drives. Once the worm spreads in the internal network, the costs are usually severe – production stoppages, redundancies, system and data restoration, and loss of reputation can add up to millions of dollars a year.
A single employee can decide
Since the worm can spread itself independently, one careless moment of a single employee is all it takes to infect the entire company network. The professionalism and creativity of the criminal attackers make recognition of the deception even more difficult and ensure that untrained employees fall victim to the assailants. The current news shows that too many critical infrastructures, particularly in the field of employee awareness, do not adequately prevent cyber attacks like these. Regular training sessions and test campaigns can significantly increase the awareness of the risks associated with the use of IT systems.
The extent of such attacks is only slowly becoming apparent to many citizens. In addition to increased media interest, large and well-known companies have increasingly become victims of ransomware. Many people perceive the likelihood of these attacks to be remote and small, and that they won’t affect their daily lives. It is only the experience of being stranded at a station or airport for several hours, or not having immediate access to electricity, water, or the Internet, that makes the threat real.
The look for the whole!
In the development of a safety concept as a preventive measure, holistic consideration is of decisive importance. In a recent assessment in the field of warehouse technology, a network segmentation of the office and industrial sectors was already in place. Nevertheless, the infestation of an ERP system by ransomware caused complete production stoppage because the industrial components were no longer supplied with real-time information.
Another example was the case of massive damage to a fire engine in a German steel mill in 2014, which began with the compromise of an office PC. With a single well-constructed email, all previous safety measures were circumvented, enabling the attackers to use the human factor to continue the damage. .This means that in addition to a well-established ISMS, the entire technical security framework (including next generation firewalls, an intrusion prevention system, endpoint security, email and web security, a security information and event management system, threat intelligence and forensics) couldn’t prevent the attack.
In the past, certain industrial sectors were considered to be isolated from the Internet and "not vulnerable." Today however, it is essential that the three areas – technical security, ISMS, and humans (employees) – are in harmony. A company must be considered as a whole. As a result, dependencies, communication processes, and employees must be included in the security concept. However, since a complete security approach can be expensive, the measures should be balanced to take into account the risk appetite (willingness or motivation to take a risk). However, a residual risk, which has been reduced by the safety measures, remains.
