ARIA SDS Solution
Enterprise-wide Network Security and Data Protection
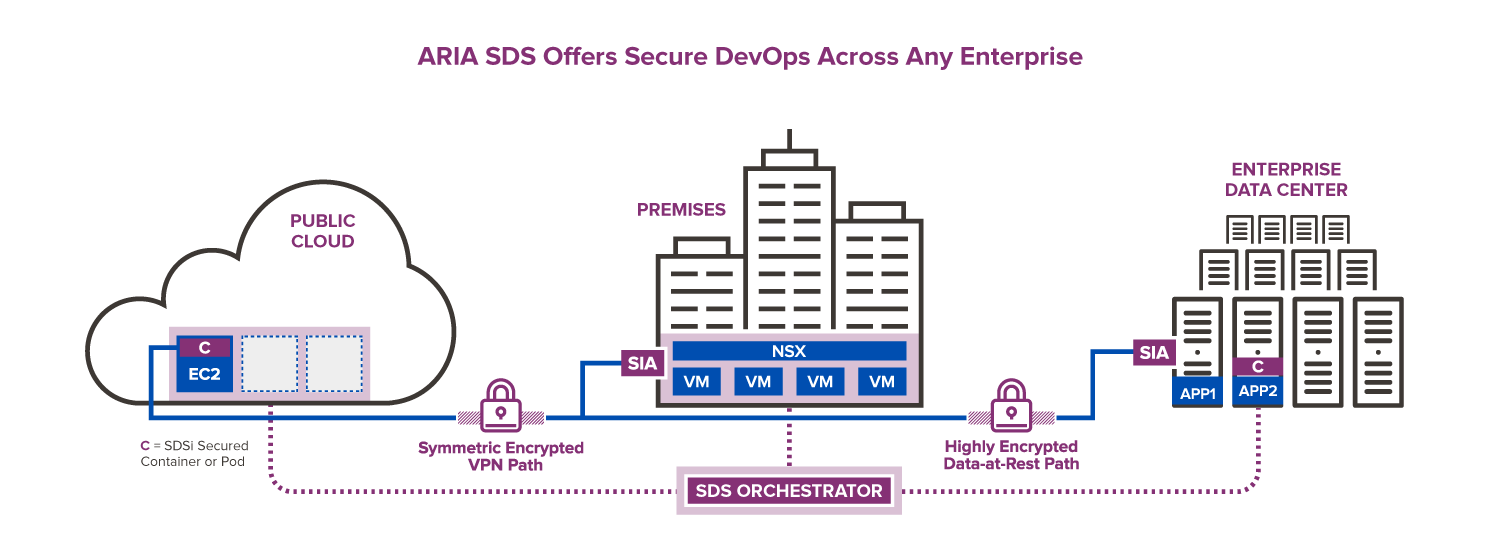
ARIA SDS Enables Accelerated Incident Response and Data Protection
The ARIA SDS solution orchestrates the security and protection of high-value business PII or PHI data from cyber attacks. As the frequency of data breaches increases, it has become critical that any potential threats are detected and verified very quickly. There are additional challenges to accurate and timely threat detection, too. These include fluid east-west communication paths, presented by the proliferation of containers, virtual machines (VMs), and cloud instances.
This leaves organizations searching for a comprehensive, yet simple solution to:
Improve the accuracy and efficiency of threat detection and remediation
Secure and protect critical data enterprise-wide
Comply with data-privacy regulations at the industry, national, and state level